In a previous post, I talked about one of the most advanced access control models to date: Risk-Adaptive Access Control. In this post, I will put this in context by taking a closer look at a variety of access control models.
Access Control Defined

Access control is all about permitting or denying access requests. An access request occurs when:
a given subject tries to access
a given resource to perform
a given action in
a given environment.
The NIST Survey of Access Control Models
The National Institute of Standards and Technology (NIST) issued a report that identifies the following access control models:
- Access Control Lists (ACLs) (subject, resource, action, N/A)
The subject is either a user or a group. In some cases it can be an application.
ACLs are hard to maintain when many users share privileges. For example, all developers should have access to the source code management (SCM) system. If the SCM is upgraded with a new feature that has its own permission, then the ACLs for all developers must be updated.
ACLs are widely available, for instance in operating systems. - Role-Based Access Control (RBAC) (role, resource, action, N/A)
Users are now generalized into roles, likedeveloper.
Roles are often not granular enough. For example, only the developers for product X should have access to the product X SCM. This can be fixed by introducing finer-grained roles, but that often leads to an explosion of roles. Sometimes there are even more roles than users in a system!
RBAC is commonly available, for instance in relational databases. - Attribute-Based Access Control (ABAC) (subject, resource, action, environment)
Everything is now generalized into attributes. Environment attributes, like the current time, are now also supported.
Attributes are often used differently in different applications. For instance, one application may name the attribute for rolerole, while another may userole-id. Or one application may use an ID into a role table as the value of the role attribute, while another uses the role’s human readable name.
ABAC is considered state of the art. - Policy-Based Access Control (PBAC) (subject, resource, action, environment)
Attributes are now harmonized across all applications of the (extended) organization. For instance, the Core and Hierarchical Role Based Access Control (RBAC) Profile for XACML defines the URNurn:oasis:names:tc:xacml:2.0:subject:rolefor the role attribute.
We’re just starting to see some PBAC implementations. - Risk-Adaptive Access Control (RAdAC) (subject, resource, action, environment)
The environment attributes now take on a much more important role. In particular, dynamic risk levels are encoded as attributes.
I know of no implementations of RAdAC, but I think we’ll start seeing them soon(ish), since they can help in the fight against Advanced Persistent Threats.
Trends in Access Control Model Evolution
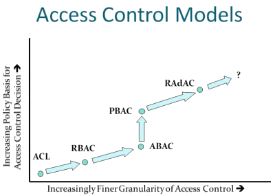
If you look closely at this mostly chronological development of access control models, you’ll find the following trends:
- Access control becomes more fine-grained
- Access control becomes more policy-based, less ad-hoc
- Access control becomes external to applications
XACML Supports All Major Access Control Models
The eXtensible Access Control Markup Language (XACML) is an OASIS standard for ABAC. Since ABAC is a generalization of RBAC, and RBAC is a generalization of ACLs, it’s not surprising that XACML can handle all of those access control models. Furthermore, PBAC is technically just ABAC. The PDP doesn’t care what attributes are used, or how they are named. Nor does it care whether does attributes represent dynamic risk levels, as in RAdAC.
So the conclusion is that XACML supports all the major access control models. This makes XACML a future-proof technology. It will easily accompany you on your journey to a more sophisticated access control model.


4 thoughts on “XACML Supports All Major Access Control Models”