 I work at EMC on a platform on top of which SaaS solutions can be built.
I work at EMC on a platform on top of which SaaS solutions can be built.
This platform has a RESTful HTTP-based API, just like a growing number of other applications.
With development frameworks like JAX-RS, it’s relatively easy to build such APIs.
It is not, however, easy to build them right.
Issues With Building HTTP-based APIs
The problem isn’t so much in getting the functionality out there. We know how to develop software and the available REST/HTTP frameworks and libraries make it easy to expose the functionality.
That’s only half the story, however. There are many more -ilities to consider.
 The REST architectural style addresses some of those, like scalability and evolvability.
The REST architectural style addresses some of those, like scalability and evolvability.
Many HTTP-based APIs today claim to be RESTful, but in fact are not. This means that they are not reaping all of the benefits that REST can bring.
I’ll be talking more about how to help developers meet all the constraints of the REST architectural style in future posts.
Today I want to focus on another non-functional aspect of APIs: security.
Security of HTTP-based APIs
In security, we care about the CIA-triad: Confidentiality, Integrity, and availability.
Availability of web services is not dramatically different from that of web applications, which is relatively well understood. We have our clusters, load balancers, and what not, and usually we are in good shape.
Confidentiality and integrity, on the other hand, both require proper authentication, and here matters get more interesting.
Authentication of HTTP-based APIs
 For authentication in an HTTP world, it makes sense to look at HTTP Authentication.
For authentication in an HTTP world, it makes sense to look at HTTP Authentication.
This RFC describes Basic and Digest authentication. Both have their weaknesses, which is why you see many APIs use alternatives.
Luckily, these alternatives can use the same basic machinery defined in the RFC. This machinery includes status code 401 Unauthorized, and the WWW-Authenticate, Authentication-Info, and Authorization headers. Note that the Authorization header is unfortunately misnamed, since it’s used for authentication, not authorization.
The final piece of the puzzle is the custom authentication scheme. For example, Amazon S3 authentication uses the AWS custom scheme.
Authentication of HTTP-based APIs Using Signatures
The AWS scheme relies on signatures. Other services, like EMC Atmos, use the same approach.
It is therefore good to see that a new IETF draft has been proposed to standardize the use of signatures in HTTP-based APIs.
Standardization enables the construction of frameworks and libraries, which will drive down the cost of implementing authentication and will make it easier to build more secure APIs.
What do you think?
 If you’re in the HTTP API building and/or consuming business –and who isn’t these days– then please go ahead and read the draft and provide feedback.
If you’re in the HTTP API building and/or consuming business –and who isn’t these days– then please go ahead and read the draft and provide feedback.
I’m also interested in your experiences with building or consuming secure HTTP APIs. Please leave a comment on this post.
 This post describes how to use the
This post describes how to use the  If you don’t call the
If you don’t call the  If you do that, you can change the cryptographic algorithm and/or implementation without issuing a patch. This is particularly valuable when a new attack on an (implementation of an) algorithm becomes available. The JCA makes it easy to configure the use of cryptography. The
If you do that, you can change the cryptographic algorithm and/or implementation without issuing a patch. This is particularly valuable when a new attack on an (implementation of an) algorithm becomes available. The JCA makes it easy to configure the use of cryptography. The 
 Another thing to look out for is that code requires
Another thing to look out for is that code requires 
 In a previous post, we discussed
In a previous post, we discussed  This is where
This is where 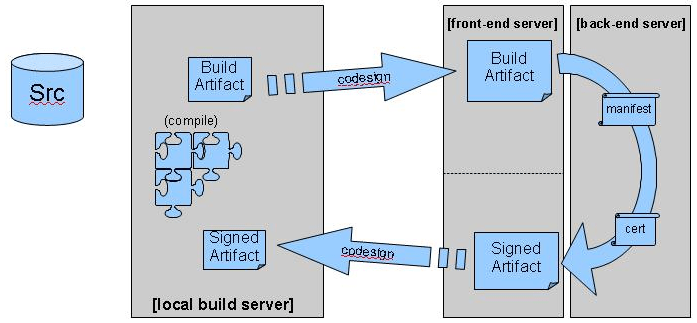
 We can alleviate this problem by
We can alleviate this problem by 
 Mobile code in source form requires an interpreter to execute, like
Mobile code in source form requires an interpreter to execute, like  Examples of active content are HTML pages or
Examples of active content are HTML pages or  A simple bug that causes the mobile code to go into an infinite loop will threaten your application’s
A simple bug that causes the mobile code to go into an infinite loop will threaten your application’s  After restricting what mobile code may run at all, we should take the next step: prevent the running code from doing harm by restricting what it can do.
After restricting what mobile code may run at all, we should take the next step: prevent the running code from doing harm by restricting what it can do.
You must be logged in to post a comment.